In 1996, a Microsoft employee Gurdeep Singh-Pall started developing PPTP (point-to-point tunneling protocol). It was published in 1999 and later the VPN technology had been improved drastically for a secure connection. The Virtual Private Network technology was developed by large companies and organizations for communication and sharing of files with security and privacy.
This network allows the employees of an organization to access the files and data of a company remotely from anywhere in the world and prevents access from unauthorized users. The concept of VPN helped the people/users to protect themselves from hackers, threats, internet censorship, and data mining. This article gives a brief note on the purpose of a virtual private network & its working.
What is a Virtual Private Network?
A virtual private network extends a private network that enables the user to send and receive the data across the public network like the internet with security and privacy. It provides privacy and security to the user’s data by building a private network connection from the public network connection (internet). It creates a safe and encrypted online connection.
These are used to hide the user’s browsing history, IP (Internet Protocol) address, geographic location, web activities, and devices being connected to the network. The other user on the same network doesn’t know what the VPN user is doing. This gives online privacy to the user.
Generally, virtual private networks are used over the least security networks like public internet. Since the ISPs (Internet Service Providers) will have a large amount of perception into a user’s online activities. If a user is utilizing an unsecured Wi-Fi access point, there might be a chance of hacking or tracing the personal data of the user. Hence, an internet user could use a virtual private network to avoid these issues on privacy.
To encrypt the transmitted data and decrypt the received data, the tunneling protocols are used in the VPN. The network address of the transmitting and receiving networks are encrypted to have better security. It is also used to protect the data that is being transmitted on mobile devices. The user can access the websites, which are restricted by location.
A virtual private network separates the user’s traffic from the public or shared network (internet) by creating a private network. It is available in both hardware and software versions. In the software version, the software client sends the request to the associated VPN server to encrypt the user’s device connections. When the connection is established, the requests for information are encrypted and sent from the user’s device to the VPN server.
The request is decrypted by the VPN server and it uses the internet to obtain the information. On getting the information, the VPN server encrypts and returns the information, which is decrypted by the software client. To understand the concept of VPN, observe the diagram shown below. The hardware version of virtual private networks is standalone devices, which can run all the required networking functions like encryption. This type of network can provide additional data security features.
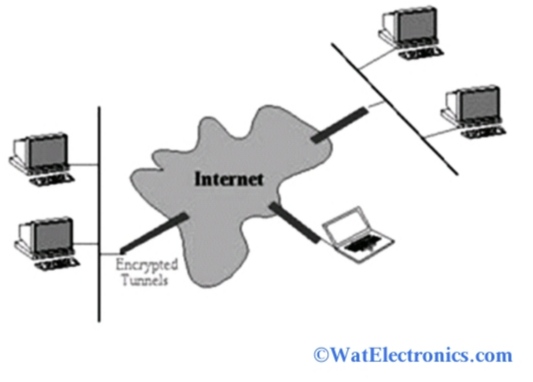
Basic Structure of VPN
Virtual private networks became a very crucial part of an organization’s security strategies regardless of business size, and geographic location. Because they provide access to the files, databases, and other network applications by the authorized remote users securely. Based on the security risks of the internet, the companies provide remote access to their employees and protect their data through a VPN connection.
A virtual private network (VPN) is considered an encrypted connection over the public internet network from a device to the network. Due to the encrypted connections, the sensitive data of the user is transmitted safely and prevents access from unauthorized people. It also allows the user to work remotely and it is widely used in corporate companies.
For a well-designed VPN connection with encryption, several methods and VPN protocols are required. There are various types of protocols used to create secure virtual private network connections. They are,
IPSec: It stands for Internet Protocol Security. It is used to create secure Internet communication across an IP network by verifying and encrypting each data packet while connecting. It is used in 2 modes. They are Transport mode and Tunneling mode.
In Transport mode, the message in the data packet is encrypted. While in tunneling mode, the whole data packet is encrypted. This protocol can be used with other protocols to improve security and privacy.
L2TP: It stands for Layer 2 tunneling protocol. To establish a secure VPN connection, it is combined with other VPN protocols like IPSec. When the tunnel is created between the two L2TP connections, the data is encrypted by using the IPSec VPN protocol to maintain secure communication between the connections.
The endpoints are located using L2TP, which creates a Layer 2 connection to the tunnel. The IPSec VPN protocol helps to make sure that data packets are exchanged securely. Sometimes, the L2TP VPN protocol can be used as a part of services provided by the ISP.
PPTP: It stands for Point-to-Point Tunneling protocol. It generates a tunnel to encrypt and confine the data packet sent between the network connections. This protocol is most widely used in Windows and also in Mac and Linux OS. This VPN protocol is used to configure the large IP system to support a secure VPN tunnel for data connections. A secure VPN tunnel can be created by configuring and then assigning a PPTP profile to the virtual user.
SSL: It stands for Secure Sockets Layer. This type of VPN protocol is used to create secure and encrypted connections over the least security networks like the internet. The standard web browsers and technologies are used in this protocol to provide remote access to the applications without any installation of extra client software by the user. When this protocol is used, the URL link starts with ‘HTTPS instead of ‘HTTP
TLS: It stands for Transport Layer Security. It is used along with SSL to secure stream-based internet traffic. The DTLS protocol is based on TLS protocol to support datagram transport and it is mostly used in VPN tunneling applications
Both TLS and SSL protocols are used to create VPN connections where the web browser acts as the client and the user is prohibited to access restricted applications instead of accessing the whole network. Online shopping websites commonly use these two protocols.
OpenVPN: It is an open-source protocol used in point-to-point and site-to-site VPN connections. It is a traditional security protocol based on TLS and SSL protocols.
SSH: It stands for Secure Shell, used to generate the tunnel to transfer the data between the network connections and also ensures tunnel encryption. The SSH client generates the connections to transfer the data from the local network port to the remote server through the encrypted tunnel.
MPLS: It stands for Multi-Protocol Label Switching. It is used in data routing to send the data from one node to another node based on the short path labels rather than using long network addresses.
The benefits and features of the virtual private network include
- It can hide the user’s IP address and location for privacy and security purposes.
- Connections are secured with data encryption
- Bypasses geo-blocked content.
- Avoids bandwidth throttling
- Advertisers or unauthorized users cannot target individual ads.
- VPNs are cost-effective.
- It supports routers and is highly encrypted and secured.
Purpose of a Virtual Private Network
The purpose of a virtual private network is to establish a secure and private path between multiple local and remote network devices. For example, an employee from a branch office can connect to the head office’s network by using VPN. And also the employee working from home (remote worker) can connect to their company’s internet to access and transfer the information with security and privacy.
Using a virtual private network is more beneficial because of encryption and anonymity, which helps to protect online activities like shopping, online transactions, sending emails, and web browsing. It provides secure remote access and prevents unauthorized users from accessing the company’s sensitive data and network.
The tunnel created by the VPN connection between the user’s local network and the end node of another network location will help to hide and protect the user’s IP address, location, and private information. This is because the VPN tunnel makes sure that the user is in another location. The virtual private network encrypts the transmitted data over the public network, which makes it unreadable to unauthorized users. It helps to hide the browsing history, IP address, location, connected devices to the user’s local network, and web activities.
The purpose of virtual private networks is to provide privacy for both public network users (internet users) and companies or businesses or organizations. Many corporate companies might utilize virtual private network technology to make sure that the authorized users are accessing their data through encrypted channels.
This technology helps the authorized user or an employee of a company to connect to a database of the same company and work from different locations. The user can access restricted resources through the VPN connection by providing some authentication factors like email address, location, passwords, biometric data, etc.
When an internet user is surfing/browsing the web, the hacker might access the information of the user including browsing data, search history, IP address, and location. The VPN can provide encryption, and anonymity features to the user to have privacy and security for their data. The user can access the geographically blocked content from another country with the VPN.
When you are using public wi-fi, the hackers might trace and steal your data on public hotspots. By using a VPN, there would be no chance of tracing due to its secure connection and you can browse with full privacy.
Before sending the internet traffic of the user like online searches, downloads, and uploads) directly to the ISP (Internet Service Provider), a virtual private network uses a routing method to route the user’s traffic through the VPN server and then transmit to the internet finally. Here it seems to be that the data comes from the VPN server but not from the personal device. This process of routing in the VPN helps to hide the IP address, location, and sensitive data of the user from hackers.
VPN Software
By using Virtual private network software, the users can connect to secure and private networks. Many corporate companies use VPN software with remote access and secure encrypted internal networks. This helps the employees to access the applications, share files and other corporate resources on the network. When they are connected to unsecured public networks like airports, libraries, etc, the personal data can be encrypted and also disables their location. The virtual private network software contains firewalls to prevent access from hackers and identify viruses and threats. The functions of virtual private network software include,
- By using encryption and security mechanisms, the devices can be connected to private networks
- Provides access to only authorized private networks
- Minimizes the network traffic to encrypt the data
- The connections are rerouted to secure private networks through tunneling protocols.
The virtual private network software is the encrypted connection between the two network devices (computers). When the user deals with the VPN service, then it is called a VPN client. When the VPN company runs the software, then it is called a VPN server. The connection is encrypted when the VPN client requests the VPN server.
There are different types of virtual private network software available for both smartphones and windows. They are,
NordVPN: It is a user-friendly app to collect and share data along with the protection of wireless devices. It doesn’t track the data and can be used to access streaming websites, messaging sites, and social media platforms with security.
OpenVPN: It is used for business purposes to secure the data for communications. It creates a secure private network and provides hassle-free client-server communications. It provides remote access to increase the speed of the internet. It manages the threats and unauthorized access of resources of the network.
ExpressVPN: It offers instant setup and is very easy to use. It provides high speed, security, and privacy while accessing web content. It provides strong privacy, security, and other features like split tunneling. In this software, an OpenVPN protocol is also used
ProtonVPN: It enables the accessing and unblocking of anonymous websites and encryption of internet connection. To provide privacy and protection, a high-speed Swiss VPN server is used.
Hide. Me: It supports both OpenVPN and IKEv2 protocols with privacy and security. The user can watch streaming live videos from anywhere in the world along with identity protection.
TunnelBear: It is a hassle-free Virtual private network software to access the web securely by hiding the IP address. The location of the user is protected from hackers.
Avast Secureline VPN: It provides online access and shares ideas from anywhere by enabling bypass geo-restrictions.
Cyberghost: It provides secure point-to-point torrenting with unblocking capability of streaming services. It allows encrypting the online connection, boosts security and digital privacy, and provides protection when connected to a new internet network.
IPVanish: This is the fastest virtual private network software for Android mobiles, which helps to access a secure internet connection.
Surf Shark: It provides secure and fast access to information on the website by making the user’s location private and securing sensitive data. It is available with two tunneling protocols like IKEv2 and OpenVPN.
Unlocator: It allows internet surfing with privacy. By using this software, the internet connection of the user is encrypted to maintain all the network activities secure.
Freedom VPN: It allows the user to hide the IP address by relocating to another location for secure online banking and transactions, taxes, streaming, and browsing. By using this VPN software, the user can access geo-blocked websites.
Hola Privacy VPN: If is a free Android application that comes with security, privacy, and encryption to access websites, videos, and media on mobile.
KeepSolid VPN: It is an Android application that protects online content. It helps to unlock the streaming video websites and access the geo-locked content and enables bypass restrictions mode.
Kaspersky VPN Secure: It allows the browsing of websites anonymously along with the protection of communication and information/data. It secures the Wi-Fi connection. It hides the IP address during online banking, video streaming, and shopping, etc.
PrivateVPN: It is an Android virtual private network software that allows access to any website and secure internet surfing. It encrypts the transmitted data for privacy and security. It supports IPSec and IKEv2 Protocols. It protects the communication channel of the internet and cannot track the user’s location.
VyprVPN: It provides secure and fast internet access and blocks the internet network traffic automatically. While accessing the content, it provides a VPN server solution with high security.
Private Internet Access: It is an open-source VPN software that provides support to Wire Guard, Socket secure (SOCKS5), points to point tunneling protocol (PPTP). It helps to protect the data of the user with a secure VPN tunnel protocol.
Hotspot Shield VPN: It helps to access online content with security and privacy. It is one of the best free virtual private network software that offers encryption of internet traffic. It helps to block the malware website and doesn’t record the browsing history to maintain privacy.
How Virtual Private Network Works?
In a virtual private network, the data to be transmitted and received between the client and internet resources, which are used by a user, is encrypted by routing a series of virtual connections over the internet. The internet protocols like HTTP, NNTP, SSH, etc are used in the encryption of data. When ports are used in virtual network connection, then the data encryption is done twice.
Here the endpoints of the VPN connection are computers, mobiles, tablets, servers, and some loT devices. The working of virtual private networks is simple and easy. When the data is transmitted from the client to a user’s VPN point, then the VPN point encrypts the user’s data and transmits it through the public network (internet). At another point of the VPN connection, the data is decrypted and sent to the internet resources like web server, email server, etc.
Again VPN point where the data is encrypted receives the data from the internet resources and is sent to another point of the user’s VPN network, which decrypts the data and transmits it back to the client.
An unauthorized user cannot access a point-to-point connection created by the VPN tunneling. The tunnel is created by using tunneling protocols, which exist over the networks. The various tunneling protocols used by the VPNs are OpenVPN and SSTP (secure socket tunneling protocol). The SSTP is used in windows to encrypt the data at various strengths.
With the use of a VPN tunnel, the device of the user is connected to another network by encrypting the data and hiding the IP address. Hence the private information of the user is hidden from the hackers and others who want to access their activities. The user’s device is connected to an exit node in another location by using the tunnel. So, it seems like the user is in another distant location.
The encrypted connections of VPN created over the internet extend the corporate network. Hence the traffic between the device and the network can be encrypted so that an employee can work remotely from the geographic location and connect to the corporate network securely. The devices like smartphones, computers, and tablets can be connected through VPN.
Actually, the virtual private network works in two ways, such as Remote access VPN and Site-to-site VPN. Observe the diagram shown below, which explains the VPN configuration in both remote access and site-to-site VPN.
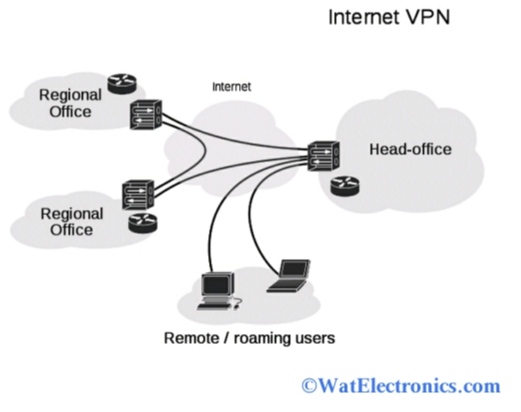
Working of Virtual Private Network
Remote Access VPN: It is also known as VPDN (Virtual Private Dial-Up Network). It is a user-to-LAN connection that most companies or organizations need to connect to the private network from different locations. When a corporation or a company wants to create big remote access, the VPN service provider gives an Internet dial-up account to connect their employees/users using ISP (Internet Service Provider).
To create a remote-access VPN, the company should be a large firm with hundreds of employees in the field. It helps to provide security and encrypt connections between the private network of the company and the users working remotely through third-party service providers. This type of secure VPN connection can be installed by using SSL VPN and IPsec VPN protocols.
A remote-access VPN connects the users working remotely and accesses the data and the applications of the company securely. It encrypts all the traffic on the network when the user is transmitting and receiving the data. It works by creating a tunnel between the company’s or organization’s network and the remote user even though the uses might be in a public location.
The traffic is encrypted to access their company’s network by the remote user with security. By utilizing remote access VPN, the company’s data can be transmitted without any disruptions and interceptions.
The remote access users are connected to the VPN server on the company or business network. The server requires the device to identify the identity before accessing the internal network resources. The remote users or private users would use VPN services to access blocked websites and bypass geographic restrictions on the internet.
Site-Site VPN: It is also known as router-to-router VPN. The multiple fixed sites of a company can be connected over the public network through the use of large-scale encryption and dedicated equipment. The cost is saved on long private leased lines because each site utilizes only one local connection. A site-to-site VPN connection is built between the offices/branches of the same organization/company, which is referred to as intranet VPN.
It also connects the company to its partners/shareholders or customers and it is called an extranet VPN. It creates an imaginary bridge between the networks at geographically distant offices of a company and connected through the internet to sustain secure and private communication.
In this type, a gateway device is used to connect the whole network of one location to a network of another location. The entire connection is handled by the gateway device so that the VPN client doesn’t require any end-node devices in the remote location. It uses IPsec VPN protocol to connect site-to-site VPN over the public network (internet).
Rather than using public networks (internet) as a transport, we can also use MPLS (Multiprotocol Label Switching) commonly. Here there is a possibility of having either Layer 3 or Layer 2 connectivity, that runs across the base transport.
The site-to-site VPN is considered an Intranet based VPN when several offices of the same company are connected to share and access the data. When several offices of one company are connected to the offices of another company by using site-to-site VPN, then it is considered an Extranet VPN.
These two types of VPNs provide various benefits for a company. They include the following,
- The geographical connectivity can be extended.
- The operational costs are reduced when compared to transitional WANs
- The transit times and travel costs for the users are reduced
- Productivity has improved.
- The network topology is simplified
- Provides an opportunity for global networking
- Telecommuter support is provided
- Provides faster ROI (Run On Investment) when compared to traditional WAN
- Provides security, reliable network, scalable network, network, and policy management.
To build any type of VPN (site-to-site VPN or remote access VPN), certain components are utilized, which include
- For each remote user, there should be a desktop client software
- There should be dedicated hardware such as a secure firewall and VPN concentrator.
- To access VPN by the remote user, NAS (Network Access Server) is used by the VPN service provider
- Private and police management center
The search history of the user is associated with the IP address of the VPN server with the help of a virtual private network. The servers of the VPN services are located in different geographic locations to make sure that users could be from any one of those locations.
The factors like speed of the user’s internet, type of protocols used by the VPN service provider, and used encryption type affect the performance of the VPN. In the business or company, the poor QoS (quality of service) of an organization’s IT department affects the performance.
The kill switches are used to support security features in some VPN connections. When the VPN connection is interrupted/disrupted, the device is disconnected automatically by the kill switch. Hence there would be no IP address exposure. The kill switches used in VPN are of two types. They are,
Active Kill Switches: When the user’s device is connected to the VPN, it prevents the device from connecting to unreliable networks. Apart from disturbances of the server, this switch is disabled when not connected to VPN.
Passive Kill Switch: These types of switch protocols are more secure than active kill switch protocols. They help to disconnect the devices from the VPN server when connected to non-VPN connections.
To ensure the security level of the connected devices, different types of VPN protocols are used. The different protocols included to secure and encrypt the data of the user are,
- IPsec (Internet Protocol security)
- SSL (Secure Sockets Layer) and TLS (Transport Layer Security)
- PPTP (Point to point tunneling protocol)
- L2TP (Layer 2 tunneling protocol)
- OpenVPN
These VPN protocols became the primary solutions to connect remote users, remote offices, and company’s partners because they provide communication access with users, employees, and partners; productivity can be enhanced by extending the network applications; cost of communication is reduced; Flexibility of the network is increased.
Advantages/Disadvantages
A virtual private network (VPN) is simple and effective for people to protect the traffic of their internet and keep their identities secure from hackers and internet service providers. The advantages and disadvantages of the VPN to create secure remote access for both home and professional purposes are discussed below.
The advantages of the virtual private network include the following.
Privacy: Disabling IP address, location, and search history would provide privacy from tracking by internet browsers, websites, companies, ISP’s (Internet Service Providers), etc. With the use of VPN, the website cannot analyze the collected data and stops the people and web browsers from accessing the connection. The information which is transmitted and received would be secure and anonymous.
Improved Security: It helps to protect the personal information that is transmitted and received by the device. It also provides file sharing with protection. So, that the file can be shared for longer periods between the devices without data corruption.
Hiding of Private Information: The hackers might use several methods to gain access to information that is entered on the website. From this sensitive information, they can hack the bank account details, credit card information, and many more. By using VPN, high-level security and privacy are possible with 256-bit encryption. This makes all the online communications visible like nonsensical, characters, and gradable text to the people who are trying to intercept.
Prevention of Data Throttling: when a specific amount of data is consumed by the user from the available data, then the Internet Service Provider (ISP) would slow down the server and hence data throttling occurs. With the VPN, the data cap can be avoided and even ISP cannot analyze how much data is being used by the user.
This is more beneficial to the employees who have data plans to access the internet from their smart devices. To increase the speed of the internet to some of the consumers, the ISP will place caps on the data.
Prevents Bandwidth Throttling: If you access the internet with slow speed on certain websites, bandwidth throttling is called bandwidth. This can happen due to the visiting of certain websites or through any other internet activity. ISP or network controllers are responsible for the slowdown of the internet. With the use of a VPN, the device’s network traffic or internet traffic can be encrypted.
The unknown people cannot see the content or websites that you are visiting. It prevents the access of the same content from your web traffic by unknowns.
Remote Access: By using VPN, the user can access the information from any location with protection. So, the productivity of the company increases because the employees no need to be in a particular location to work. The VPN is a remote access network.
Accessing bypass geo-blocked Services: Most of the entertainment websites will have restrictions to access the content in specific locations. This can happen when the content is available only in a particular location. With the help of a VPN connection you can access the websites and web applications anonymously without being traced and irrespective of location.
With the VPN connection, you will get another IP address to browse the internet and for another online internet activity. For Example, Netflix allows access to streaming content from a particular location. The VPN connection service will indicate that your Netflix application is with the same IP address that is permitted to access. Hence the VPN can disable all the geographical restrictions to access maximum internet entirely.
Bypass Blockers and Filters: By using VPN services, you can access the blocked websites and through the established internet filters. Due to this reason, the VPN services are available in many counties and used by more people where there is a use of internet censorship.
Anonymity: The VPN connection helps to keep the user’s information and server’s data safe and secure without being accessible by unknown users.
Reduced Cost: with the use of a VPN connection, the cost of network maintenance services can be reduced because the outsourcing of third-party service providers supports a low-cost network structure to many clients/users.
The other benefits of using VPN services are,
- The network scalability
- Enhanced performance
- Reduced long-distance telephone charges
- Accessing regional sports available in particular locations.
Before using the VPN, it is necessary to know the disadvantages also. Here are some of the drawbacks of the VPN discussed below.
Low Internet Speed: With the VPN connection, the user might experience a slower internet speed due to the rerouting, maintenance of a certain amount of bandwidth, and encryption of data. But these days, VPNs are available with minimal loss of connection speeds.
Complex Connection: It is very difficult to set up a VPN connection because the physical components used in the connection are difficult to understand. Hence you have to choose the best VPN service provider with the necessary support services.
VPN Blocking Software: To charge people based on the location, some e-commerce websites use the VPN blockers software to find and prevent the users from using VPN connections. The website access can be blocked if they find that the user is using a different IP from a different location than the original.
Dropped Connections: Sometimes the VPN might drop the connection and lose connectivity.
Illegal: Some countries blocked the VPN and don’t allow the users to use this private service. Because they consider that the use of private network services is illegal. So, before getting a VPN connection, check the countries list and make sure that the use of VPN service is legal in your location.
Encryption Issues: Select a reliable VPN service with high encryption knowledge to quickly resolve performance issues.
Know more about Backpropagation Neural Network MCQs, Transmission Media MCQs , Virtual LAN MCQs, Network Devices MCQs.
Please refer to this link to know more about Backpropagation Neural Network, Bus topology & Transmission Media in Computer Networks.
Thus, this is all about an overview of Virtual Private Network – definition, working, purpose, advantages, and disadvantages. These days, most private companies utilize the technology VPN to send encrypted data over the network with confidentiality. It is recommended to add SDP (Software Defined Parameter) to the company’s VPN connection to reduce the risk of hacking and threats. Here is a question for you, “What are the applications of Virtual Private Networks? “