A reference model like OSI is frequently used in mode communication, which states that how the data is communicated between two software applications in the computer. This model comprises 7 layers where each layer has its own security protocols and responsibilities. This was developed in the year 1984 by ISO (International Organization for Standard) and today the model is defined as an architectural approach of inter-computer communications. As every layer in the OSI model is aligned with specific tasks and functionalities, today the article discusses on Transport Layer in the OSI model, its responsibilities, functions, security, and devices.
What is Transport Layer?
The transport layer in a computer network is the fourth layer from the top in the OSI model. The main function of this layer is to acknowledge information receiving from its above layer and divide it into manageable units and transmits the divided information to the Network layer and it even makes sure that the entire divided information reaches correctly to the destination. The layer ensures for efficient transmission of data and in the approach that separates its above layers from unavoidable modifications in the hardware technology.
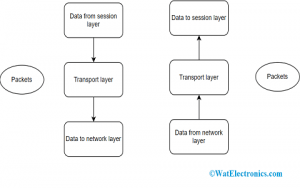
Transport Layer
The layer even decided what kind of service to be provided for the Session layer and finally to the network users. The major kind of transport connection is the zero error point-to-point channel which transmits messages in the same order as what they are broadcasted.
It establishes a logical type of communication in between various application processes operating of various host providers. Even though the application processes are not connected in a physical manner, they use the logical communication offered by the transport layer for the transmission of messages to each other.
Elements of Transport Layer
The general protocols employed by the transport layer in augmenting its functionalities are User Datagram Protocol, Datagram Congestion Control Protocol, and Transmission Control Protocol. The responsibilities/elements of the transport layer are explained as below:
The process to Process Delivery
As data link layer need MAC address (containing 48-bits address in then NIC for each host device) of the source to destination hosts for proper frame delivery and network layer need Ip address for correct packets routing, in the same approach transport later need a port number for properly delivering chunks of information to the specific process all among various processes operating on a specific host. The port number is a 16-bit address which is used for the identification of client and server program distinctively.
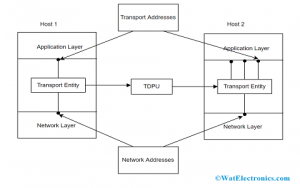
Communication Process
Multiplexing & Demultiplexing
The process of multiplexing allows synchronized usage of various applications through the network that is operating on the host. The transport layer offers the methodology that permits the transmission of packet streams from multiple applications at the same time on a network. The transport acknowledges the received packets from various processes which are differentiated by port numbers and then transmit those to the network layer after the addition of suitable headers.
This is the process of multiplexing carried out by the transport layer. Whereas demultiplexing is the process that is performed at the receiver section in order to get the information receiving from multiple processes. Transport gets chunks of information from the network layer and then broadcasts to the specific process operating on the receiver’s device.
End-to-End Connection
The transport layer also holds the responsibility of generating an end-to-end connection between various hosts and for this connection it mainly uses user datagram protocol and transmission control protocol. TCP is a reliable and connection-adapted protocol that makes use of handshake protocol in order to create a strong connection between the host devices.
Also, TCP makes sure of safe delivery of information and is implemented in multiple applications. On the other hand, UDP is the deported and inaccurate protocol that makes sure of good data delivery. It is applicable in situations that have little issues regarding an error or flow handling and need to transmit huge information such as video conferencing. It is even employed in multicasting protocols.
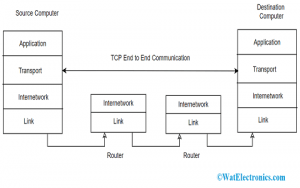
End to End Communication in Transport Layer
Data Integrity and Error Rectification
The information that is coming from the application layer might have errors and those are checked by the transport layer through the calculation of checksums and by detection codes. It analyses whether the received information is corrupted or not and through NACK and ACK services, it notifies the sender if the information has arrived or not and ensures data integrity.
Congestion Control
This is the condition where multiple sources on a network try to transmit information and the router buffers start out to overflow because of packet loss. Due to this, packets transmitted from the sources get increases and the congestion is more increased. In this scenario, the transport layer shows the mechanism of congestion control in multiple approaches.
It employs an open-loop type of congestion control to stop congestion and a closed-loop type of congestion control to totally eliminate the situation of congestion in a network once it takes place. TCP also provides an AIMD method for controlling congestion.
Full Duplex Service
TCP also provides the feature of Full Duplex which means that information flow takes place in both directions synchronously. In order to accomplish this service, every TCP needs to possess both transmission and reception buffers so that the segments flow happens in both directions. TCP is considered a connection-adapted protocol.
For instance, process A needs to transmit and accepts the information form process B, then the step to achieve this process are:
- Create a connection in between the TCP ends
- Information gets exchanged in both the TCP ends in both directions
- Finally, the connection is closed
Flow Management
The transport layer also offers a flow management approach in between different layers in the IP/TCP model. TCP even avoids data loss because of the quick sender and gradual receiver by the implementation of few flow-controlled methods. It even employs the sliding window protocol method that is achieved by the receiver section by transmitting a window back to the sender by notifying the information size that it can receive.
Addressing
In correspondence to the layered approach, the transport layer communicates with the operation of the session layer. Almost all the protocols merge presentation, application, and session layer protocols as a single layer which is termed as the application layer. In these scenarios, the delivery to the session layer corresponds to that the data is delivered to the application layer.
The information which is produced by the application in one device has to be broadcasted to the suitable application on another device. To establish proper broadcasting, the transport layer provides addressing.
The layer offers a user address that is mentioned either as a port or station. The variable of the port signifies that a specific TS customer of a corresponding station called TSAP (Transport Service access point). Every station holds only one transport entity. The protocols in this layer should be aware of the upper-layer protocols that have communication with it.
Devices
The transport layer is mainly accountable for good process-to-process communication. A few of the transport layer devices are explained below:
Firewall – This is the device that is intended to avoid any kind of unauthorized access either to or from the private network. Few of the operations managed by firewall devices are of packet filtering and also functions as a proxy server.
Gateways – In the domain of computer networks, a gateway is the device that is the component of two network devices that uses various protocols. It is also a protocol converter where it converts one protocol into another one. A router is considered a special type of gateway.
Security at Transport Layer
The importance of Transport Layer Securities (TLS) is that they are intended to provide enhanced security at the transport layer. TLS was initially originated from a security protocol which is Secure Service Layer (SSL). It makes sure that no other external parties listen to their messages.
The main advantages of TLS are:
- Encryption – TLS helps to provide enhanced protection for the transmission of messages through encryption procedures.
- Algorithm Flexibility – It offers activities for protection procedures, encryption, and hashing algorithms that are used at the time of secure sessions.
- Interoperability – As TLS mostly functions with web browsers consisting of Microsoft IE and with many operating systems and internet servers.
- Simple Deployment Procedures – Most of the applications such as TLS/SSL can be easily deployed on windows server 2003 OS.
- Usability – As the implementation of TLS is under the application layer, many of its functionalities are totally not visible to the customers/clients.
How TLS Operates?
The connection between server and client is done through TCP and assumes that the client is something. The client transmits the below specifications and those are:
- A version of SSL/TLS
What is the type of cipher that suites for it and which compression procedure does it follows?
The server initially verifies what is the highest version of SSL that is supported by both of them and then selects one cipher suits from one of those and as an option chooses a compression process. Then after this selection, fundamental setup is done and the server provides its certificate.
This has to be endorsed either by the external party of the client or by the client itself. Upon verification of the certificate and being specific that the server is truly the choice that it claims and then a key is exchanged. This might be a public key termed as ‘PreMasterSecret’ or just nothing based on the cipher suite.
Now, both the client and server compute the key to move ahead with symmetric encryption. The handshake is completed and both the hosts can have secured communication. In order to close the connection, TCP connection from both ends gets to know that the connection was not properly closed. The connection should not be compromised through this way merely disrupted. This is how TLS security is operated.
As the transport layer has better authentication procedures and advanced algorithms, this is considered more effective and secured. In the terms of efficiency, the transport layer also provides backward compatibility even for the earlier generation devices. And this is all about the transport layer where we got to know about its elements, responsibilities like multiplexing, flow control, addressing, and its devices. Also, the other crucial concept to know is what is the transport layer segment format?